Recovering from Hacked Gmail
This morning started like every other morning except for the fact that I noticed a strange email from myself to myself (work email). It seemed that I had emailed myself and a few other people that started with “B” from my address book. First response? Oh crap, my gmail account was hacked. Sure enough, a few minutes later as I logged into my account I saw about 20+ emails. Half were mail delivery failures and the other half were all my wonderful friends informing me that I sent something in error or the simple truth I already knew which was my account was compromised.
Thanks to a quick Google/Twitter search, I saw that I was not alone in the matter. Therefore, I wanted to provide some details on what I did to minimize the issue overall.
First, I tried to see the extend of the breach in my gmail. Based on the emails that I saw, it seemed that the hack essentially spammed my entire contact list (about 250+ people). I quickly emailed my first group of people (family as I just didn’t have the best faith for them not to click on anything I sent). Then I selected my entire contact list and began to compose a generic email to the masses. Hopefully I could catch enough people in time before they clicked on the link. I didn’t get to everyone in time but most people were, thankfully, aware of what the email could have been so they ignored it (probably like they did for any other legitimate email I had sent them before).
With email sent, next item on the list was to change my password. Yes, as a “security professional” I know that I should change my passwords every 90 days and make them difficult to guess. I had the second part of that requirement down. Just not the first. I had been using the same password since my first use with Gmail. Yes, I was asking for this to eventually happen.
With my password changed, I took the next steps to see how I could prevent this further from happening. Here are some additional steps I took. These don’t guarantee that I’ll be hit again but at least it will help.
- How Can I Check if My Account Has Been Compromised?
- How to Change Gmail Password?
- How To Change Password Recovery Options?
- What Other Gmail Settings Should I Review for Hacking?
- How do I setup 2 Factor Authentication?
How Can I Check if My Account Has Been Compromised?
At the bottom of your gmail account, you will find information on the last known logged in session (last time someone accessed your account).
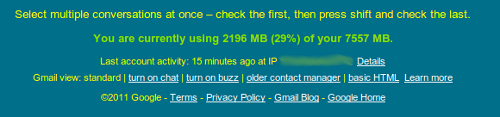
If you click details, a pop up window will appear providing the last several locations where an account was accessed. I would suggest becoming familiar with this list so you know what is out of the ordinary. Google will inform you sometimes when an account was accessed outside of your normal locations, but you cannot always trust Google to catch it. In my case, when I looked at the list I noticed instantly that the location of Spain was listed. Not a normal location for me to access my account since I’m a standard US resident. Some of the locations may not be familiar to you but these could be based on you connecting to your account from a phone or some other means. This is why I stress to become familiar with this list.
How to Change Gmail Password?
Because of the new Google toolbar, this was not the easiest for me to find at first. Maybe I was just frustrated by the terrible start to my day.
- On the top right corner of the gmail screen is a new Google bar. Click the cog.
- Select “Mail Settings”.
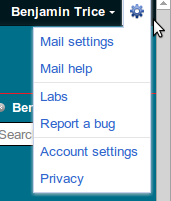
- Click the “Accounts and Import” tab.
- Click “Change password”
The instructions from here are pretty clear. Google will even provide you with visual queues to the strength of your password. Please try to follow these thoughts on the creation of this new password:
- Password should not be easy to guess
- Password should not be an incremental value from the previous password
- Password contains a combination of numbers, letters, and special characters
- Passwords should be closer to the max number of characters that the password field allows. I.E. if it allows 6-8, then try to make a password closer to 8 than 6. The more characters and complexity of the password, the better.
How To Change Password Recovery Options?
This step is important if you ever forget your password. It is Google’s way of providing a secondary method for retrieving a password.
- On the top right corner of the gmail screen is a new Google bar. Click the cog.
- Select “Mail Settings”.
- Click the “Accounts and Import” tab.
- Click “Change password recovery options”
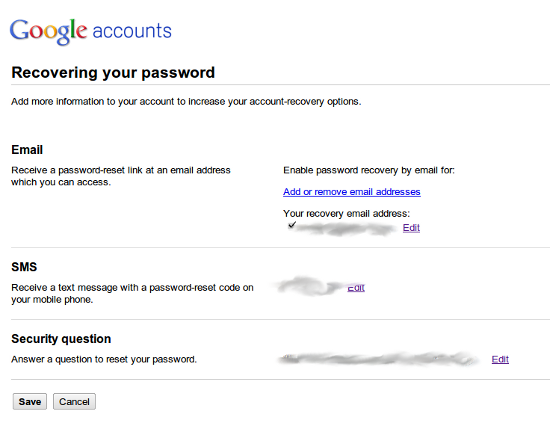
From here, you are given 3 options: Alternative Email Address, SMS Messsage, and Question Response. I suggest using all 3 options given to you.
What Other Gmail Settings Should I Review for Hacking?
Gmail has a few helpful settings for allowing one to control different areas of your account. However, these are areas that others can use as well once your account has been compromised.
- On the top right corner of the gmail screen is a new Google bar. Click the cog.
- Select “Mail Settings”.
- Click the “Accounts and Import” tab.
- Verify that no new items have been added or modified under “Grant access to your account” and “Send Mail as”.
- Click the “Forwarding and POP/IMAP” tab.
- Disable both POP and IMAP.
Steps 5 and 6 are optional, but they can be potentially another way for someone to retrieve messages from your account. As I don’t use a desktop based program (Outlook, Thunderbird, etc.), I don’t mind disabling these options.
How do I setup 2 Factor Authentication?
First, what in the world is two factor authentication? Well, it is another way to verify the person attempting to access a site is who they say they are. This is performed by requiring two forms of identification: 1) Something you know (password) and 2) Something you have (a code). For those corporate work professionals, you would be familiar with this through the use of RSA tokens.
With Gmail, this means that when I login to my account from a computer, I provide my password and a code that is generated for me on my cell phone. It works even if I don’t have access to the data network and I always have my phone with me. I know what you are thinking though. I have to enter a new code every time I login? Well, yes, but you do have the option to tell the computer to remember you for 30 days. In 30 days I’ll need to enter a code again. Simple enough. Annoying at times, but worth it so I don’t have my account hacked and several high ranking bosses at work receive the spamming emails.
- On the top right corner of the gmail screen is a new Google bar. Click the cog.
- Select “Account Settings”.
- Click the “Using 2-step verification” link located under Personal Settings / Security (right side of the page).
- Follow the steps to setup 2 factor. They are pretty straight forward.
Note: 2 Factor Authentication is not setup for all Google Apps (Picasa, Google Talk, Mobile Gmail, etc.). For these applications, you will need to setup application specific passwords. This is also very easy to do and can be found following the same steps above but click on “Authorizing Applications & sites”. With this change, you can revoke access to applications at any time which provides better security protection as well.
Posted under Internet